Chapter 2-2: Data Dictionary Concepts |
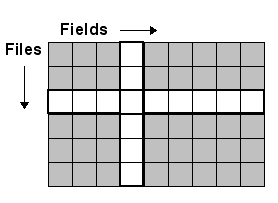
Database Security Security refers to the function that protects programs and data from unauthorized access and/or modification. Within the APPX environment, security is optional and can be designed, implemented, or modified at any time during the life of an application. Security in the Data Dictionary Within the APPX data dictionary, you use field and file security specifications to control which users can view and modify data presented in images in applications. The figure below illustrates the effect of each of these security definitions within a sample file containing six records of 13 fields each. To secure fields in images in input and output processes, you assign two separate security codes in the dictionary: Read rights govern whether or not a user can see the contents of a field as defined in an image, either input (transaction entry, maintenance, or inquiry screens, for example) or output (journals, lists, or reports). If a user does not have read rights to a secured field, the contents of the field are invisible and not modifiable. Modify rights govern whether or not a user can change the contents of a field. A user with modify rights is automatically granted read rights, regardless of the value in the read security specification. If the user does not have modify rights but does have read rights, the contents of the field are visible but not modifiable.
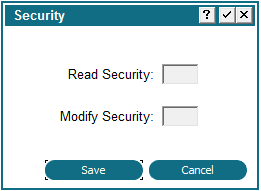
Field- and File-Level Security in the Data Dictionary The APPX dictionary includes read and modify security specifications for domains, files, fields, and work fields, and records. Domain specifications function as defaults for all fields and work fields that reference them. File specifications control read and write access to the file. Field security specifications can be defined if the domain specification is blank. If security specifications are blank at all levels, access to the field is unrestricted. Work field security specifications can be defined if the domain specification is blank. If security specifications are blank at all levels, access to the field is unrestricted. Record security is discussed in the Record Protection section of this manual. You define security in the data dictionary by selecting the Security Button from the Domains, Files/Fields, Fields, and Work Fields screens, which accesses the Security overlay shown in the figure below. From this overlay, you can select the security option. Upon completion, you are returned to the screen from which you selected the Security option.
Security Overlay APPX does not permit you to secure a specific field or group of fields on a specific record. Field-level security applies equally to all records in a file, and file-level security applies to every field in a file. Field security specifications, unlike the file security specifications, do not restrict access to fields from the application design facility. For example, a user with design rights could define statements to modify values in secured fields, or to load the contents of secured fields into unsecured work fields. The contents of a secured file, however, cannot be accessed with statements. Assigning Security Codes APPX's security facility was designed to provide maximum flexibility. As a result, there are no incorrect methods of assigning security codes. There are, however, methodologies that are more efficient or easier to establish and maintain than others. |
Application Design Manual "Powered by Appx Software"139 ©2006 By APPX Software, Inc. All Rights Reserved |